This article has been machine-translated from Chinese. The translation may contain inaccuracies or awkward phrasing. If in doubt, please refer to the original Chinese version.
This review covers: Chapter-5: Public Key Cryptography Chapter-6: Key Management Chapter-7: Security Protocols
Content Overview
Chapter-5: Public Key Cryptography The encryption key in public key cryptography is public, which solves the key management and distribution problem. This chapter introduces several typical public key algorithms, including the RSA algorithm based on the large number factorization problem, and the Diffie-Hellman / ElGamal cryptosystems based on the discrete logarithm problem.
- RSA public key cryptographic algorithm
- Diffie-Hellman key agreement mechanism
Chapter-6: Key Management Key management is the core of cryptographic technology application. This chapter explains key management techniques for symmetric key and public key cryptography applications.
- Key management and distribution in symmetric cryptography
- Key management and application in public key cryptography -- Public Key Infrastructure PKI
- Public key carrier in public key infrastructure -- Digital certificates
Chapter-7: Security Protocols This chapter explains the concepts of security protocols and the classification of typical security protocols in the network layered architecture. Focus is on the Virtual Private Network protocol IPSec and Transport Layer Security protocol TLS.
- Mechanisms for implementing security protection at each layer of the network architecture
- IPSec VPN protocol security protection mechanism and working process
- TLS transport layer security protocol protection mechanism and working process +++
Public Key Cryptography
RSA Public Key Cryptographic Algorithm
- RSA is a classic public key cryptosystem, named after its designers Rivest, Shamir, and Adleman, publicly described in 1978
- RSA can be used for both encryption and signing, with wide applications
- The RSA algorithm includes two keys: public key and private key
- The public key can be known by anyone and used to encrypt messages
- Messages encrypted with the public key can only be decrypted using the corresponding private key
- The RSA public key cryptosystem includes 3 components: key generation, encryption, and decryption.
Key Generation
User A performs the following work:
- Select two prime numbers and
- Randomly selected, with similar bit lengths
- Compute
- is used for modular arithmetic in both public and private keys
- Compute the Euler's totient function
Euler's totient function: In number theory, for a positive integer , Euler's totient function is the count of positive integers less than or equal to that are coprime to . (Generally )
An important theorem: if p and q are coprime numbers, , then . In particular, if p and q are both prime, then .
Extended reading: Euler's Totient Function Formula and Analysis
- Compute the public key exponent
- must be an integer from the Euler's totient function
- is coprime to (i.e., and share no common factors other than 1)
- Compute the private key exponent
- must satisfy the congruence relation (ps: modular arithmetic theorem)
Congruence theorem: Given a positive integer , if two integers and satisfy that is divisible by , i.e., yields an integer, then integers and are said to be congruent modulo , written as . Congruence modulo m is an equivalence relation on integers.
In other words, can only be divided by - The Extended Euclidean Algorithm is typically used to quickly compute (finding the modular multiplicative inverse)
- is kept secret as the private key exponent
- must satisfy the congruence relation (ps: modular arithmetic theorem)
- User A publishes the public key
An Example
Choose such that is coprime to , i.e., and share no common factors other than 1. We can choose a prime , then verify they don't divide each other. (3120 is not divisible by 17, so it's OK) Compute . This is actually computing the modular multiplicative inverse of e modulo . Since , i.e., 46801 divided by 3120 has remainder 1. Therefore:
- Public key:
- Private key:
Encryption and Decryption Process
User B encrypts message M and sends it to User A. The encryption process is as follows:
- Convert message M to an integer
- Compute , i.e., (public key encryption)
User A receives message and performs the following:
- Compute , i.e., (private key decryption)
- The computed m can be converted back to message M
RSA Security Guarantee
- RSA's security relies on the large integer factorization problem. Factoring a large integer into prime factors remains a mathematically difficult problem.
- However, integers exceeding 200 decimal digits can currently be factored, so it is recommended that RSA's modulus n be at least 1024 bits long.
Diffie-Hellman Key Agreement Mechanism
Can public information be transmitted over an insecure communication channel to ultimately enable both parties to obtain secret information? This requires key agreement.
- The D-H key agreement mechanism can establish a shared secret for two entities over an insecure channel. The negotiated secret can be used as a key for subsequent symmetric cryptosystems.
Too lazy to write more, go read Diffie-Hellman Key Agreement Algorithm & Man-in-the-Middle Attack
Key Management
Modern cryptographic technology requires cryptographic algorithms to be public, so key security is the key to cryptosystems and the most difficult problem in cryptographic applications.
- Symmetric cryptosystem: Keys are held by the shared parties (two or more) and are highly confidential.
- Where should keys be generated?
- How to distribute them?
- How to update them periodically?
- How to handle key compromise?
- Public key cryptosystem: Public keys are held by shared parties but are not highly confidential.
- How are key pairs generated?
- Who generates them?
- How are private keys stored?
- Is the public key currently in use valid and correct?
- How to update the key pair if the private key is compromised or lost?
Key management is the secure control of the entire lifecycle of keys from generation to destruction, covering key setup, generation, distribution, storage, loading, use, backup, recovery, extraction, update, revocation, destruction, and protection. Its core objective is to ensure that key security is not threatened.
- Symmetric cryptosystem: Uses a Key Distribution Center
KDCas the Trusted Third PartyTTP - Public key cryptosystem: Certificate Authority
CA
Some basic requirements for key management:
- Key generation: The key generation algorithm and its implementation are fundamental to key quality. Key generation should have good randomness.
- Key length: Determines the key space size and cipher strength.
- Key storage:
- Soft protection (password-encrypted files)
- Hard protection (smart cards, USB Keys, and other storage devices)
- Key update: Keys should have a validity period.
- Key revocation: Keys should be promptly updated when lost or under attack.
- Session Key: A one-time use temporary key.
Symmetric Key Management and Distribution
In a symmetric cryptosystem with N users, if pairwise key sharing is required, the total number of keys needed is N(N-1)/2.
- Simple key distribution: One user generates the key and distributes it to other participating entities through a secure method.
- When there are many users, simple key distribution is not feasible.
Using public key cryptography to achieve dynamic negotiation and update of symmetric shared keys:
- Using the D-H key agreement protocol to generate shared keys
- Using the other party's public key to encrypt and transmit session keys
Hierarchical Key Usage
Key classification and hierarchical management: Improving security
- Using different keys for different purposes:
- Encrypting session messages
- Encrypting other keys
- Computing message authentication codes...
- Hierarchical management: Entities first share a master key, then use specific algorithms to generate multiple subkeys based on the master key.
Key classification examples:
- Master Key
MK: At the highest level of the key hierarchy- Generally established manually
- Or through key agreement mechanisms
- Or using public key cryptosystems to complete master key agreement or transfer.
- Key Confirmation Key
KCK: Used in communications to generate message authentication codes, confirming generated keys or messages. - Key Encrypting Key
KEK: Used to encrypt other keys in key transport protocols. - Temporal Key
TK: Also called Session Key. Used to encrypt user communication data.
Public Key Infrastructure PKI
How can one conveniently obtain the needed, valid, and correct public keys?
- The solution is Public Key Infrastructure PKI (Public Key Infrastructure)
PKI Overview
- PKI is a general-purpose security infrastructure that implements and provides security services using public key cryptographic technology, and is one of the core technologies in the information security field.
- PKI publishes valid entities' public keys through an authoritative third-party institution -- the Certificate Authority CA -- by issuing digital certificates.
- A Digital Certificate is a special electronic document (also called an electronic credential) that includes information about the public key holder (called the subject), their public key, validity period, usage methods, and other information. A digital certificate binds the certificate holder's identity to their public key.
- Integrity protection of digital certificates:
- The binding relationship between the holder's identity and their public key cannot be tampered with
- Solution: The CA digitally signs the digital certificate
- PKI is a method, process, and system for issuing digital certificates by authoritative institutions and managing digital certificate usage by communication entities.
- Has trusted authorization centers and certification authorities -- CA
- Responsible for certificate generation, management, archiving, issuance, revocation, and other certificate management tasks
- Provides comprehensive security services to users
- The separation of PKI security service implementation and application is an important characteristic of it being an infrastructure.
PKI Functions
PKI functions include digital certificate management and services based on digital certificates.
- Certificate management: The core work of PKI, handled by the CA
- Certificate application
- Certificate generation
- Certificate publication
- Certificate revocation
- Certificate renewal
- Certificate backup and recovery
- PKI services: Establishing trusted digital identities for certificate holders, and providing authentication, authorization, and digital signature services by combining digital identities with cryptographic mechanisms
- Confidentiality services
- Integrity services
- Authentication services
- Non-repudiation services
- Timestamping
- PKI cross-certification: Interconnection and business integration of different PKI systems
- Establishing trust relationships between PKIs, enabling users of one PKI to verify certificates of users from another PKI
- Different PKI CAs issue cross-certification certificates to each other: the certificate issuer is one CA, and the certificate subject is another CA, establishing trust relationships between different security domains.
PKI Architecture
- A complete PKI system consists of the Certificate Authority CA, Key Management Center KMC, Registration Authority RA, Directory Service, Certificate Application Service, and Security Authentication Application Software.
- Large-scale PKIs can have multiple CAs organized in a tree hierarchy, forming a trust chain based on a top-level CA (root CA). PKI architecture diagram
Digital Certificates
A digital certificate is the carrier of an entity's public key, used to bind a public key to an entity's identity. A digital certificate is an electronic document consisting of 3 parts, with its ASN.1 description as follows:
Certificate::=SEQUENCE{
tbsCertificate TBSCertificate, //Certificate subject data
signatureAlgorithm AlgorithmIdentifier, //Signature algorithm
signatureValue BITSTRING //CA's signature
}Digital Certificate Structure
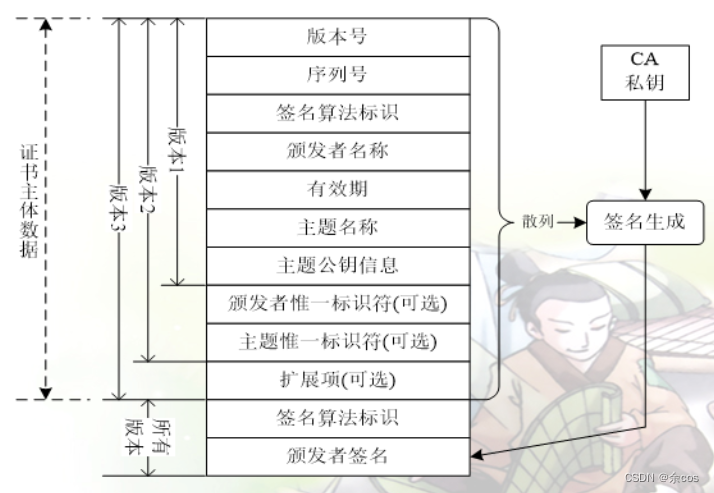
Certificate subject data includes:
- Version number: 0 (v1), 1 (v2), 2 (v3)
- Serial number: Certificate unique identification number
- Signature algorithm identifier: The signature algorithm and HASH algorithm used by the CA to sign the certificate
- Issuer name: Identifies the certificate issuer using issuer attribute sets
- Validity period: Certificate start time and expiration time
- Subject name: Certificate holder attribute set
- Subject public key: Public key algorithm and public key value
- Issuer/Subject unique identifier: Optional
- Extensions: Additional attributes of the subject and public key, optional
Security Protocols
Security Protocol Overview
What is a protocol?
- A protocol is a series of definite steps executed by peer entities (two or more parties) to accomplish a task; it is a set of rules that protocol entities must jointly follow
- Protocol steps (or rules) are explicitly defined
- A protocol must be complete
What is a security protocol?
- Protocols that use cryptographic technology to provide various security services in networks and distributed systems to achieve specific security goals are called security protocols or cryptographic protocols
- Two most fundamental types of security protocols: entity authentication protocols and key agreement protocols
Security protocols at each layer of the network protocol stack: In network environments, security services can be implemented at different network layers, as follows:
| Layer | Security Protocols |
|---|---|
| Application Layer | HTTPS, SSH, PGP, Kerberos, SET, MIME |
| Transport Layer | TCP, UDP, SSL, TLS, SOCKS5 |
| Network Layer | IPSec |
| Data Link Layer | PPP-PAP/CHAP, WEP |
Data Link Layer Security Protocols
PPP-PAP
PPP-PAP (Password Authentication Protocol - Point to Point Protocol)
Password Authentication Protocol
PAPis a link control sub-protocol ofPPP. After peer entities establish an initial connection, it uses two-way handshake to implement entity authentication.
- The authenticated party continuously and repeatedly sends "User ID/Password" to the authenticating party
- Until authentication receives a response or the connection terminates.
PAP authentication passwords are transmitted in plaintext over the link, making it unable to prevent eavesdropping, replay, and other attacks. It is a weak authentication method.
PPP-CHAP (Verifying Peer Entity Identity)
PPP-CHAP (Challenge Handshake Authentication Protocol)
Challenge Handshake Authentication Protocol
PPP-CHAPis a sub-protocol within thePPPprotocol suite. It uses a three-way handshake to verify peer entity identity.
- The authenticated party sends an "identifier" to the authenticating party
- The authenticating party sends a "challenge" (Challenge: random number) message to the authenticated party
- The authenticated party uses the challenge and password (pre-shared by both parties) to jointly compute a hash value as a response
WEP (Providing Protection for Wireless Links)
WEP (Wired Equivalent Privacy)
Wired Equivalent Privacy
WEPis a wireless LAN security protocol defined in the IEEE802.11b standard. WEP provides protection for wireless links at the data link layer, implementing mutual authentication and confidential data transmission between wireless nodes.
- WEP uses shared key authentication and RC4 stream cipher algorithm to encrypt data frames
- WEP is optional in 802.11 and has been found to have defects. It has been replaced by a new protocol (IEEE802.11i) in newer 802.11 standards.
Application Layer Security Protocols
MIME / S-MIME (Email Security Protocol)
Multipurpose Internet Mail Extensions / Secure-MIME
MIMEMultipurpose Internet Mail Extensions defines email message formats for convenient message exchange between different email systems. It allows emails to contain any type of file, such as text, images, audio, video, and other applications.
S-MIMEis the secure version of MIME, providing a secure email mechanism. Based on the MIME standard, S-MIME provides email security services for electronic messaging applications, including authentication, integrity protection, and data confidentiality.
PGP (Pretty Good Privacy)
- An open-source application for email, stored data encryption, and digital signatures
- PGP is based on RSA public key encryption, implementing encryption protection for emails, as well as source authentication and non-repudiation protection based on digital signatures.
- PGP supports key management servers, but its certificate model differs from X.509
- The PGP model allows multiple, independent, non-specially-trusted individuals to sign "name/key" associations to prove certificate validity
"Given enough signatures, the name/key association is trustworthy because not all signers can be 'bad'", the so-called "Web of Trust" model
SET (A Secure Electronic Payment Model)
SET (Secure Electronic Transaction)
- A secure electronic payment model used for e-commerce security assurance
- Solves trust and secure transaction issues between merchants, consumers, and banks in B2C mode
- Involves transaction agreements, information confidentiality, data integrity, data authentication, digital signatures, and other issues in e-commerce transactions
Virtual Private Network Protocol IPSec
How to achieve secure data communication at the IP layer? VPN (Virtual Private Network)
- VPN is a private network built on public networks (such as the Internet)
- Achieves secure transmission of important data by establishing secure channels between two systems
- VPN can be implemented on network devices such as routers, switches, or firewalls
- VPN can help remote users, company branches, and business partners establish trusted secure connections with internal networks, ensuring data transmission security
- Using VPN technology to build virtual enterprise networks over the Internet can greatly reduce enterprise operating costs and enhance competitiveness.
IP layer security protocol IPSec (Internet Protocol Security)
- IPSec is a VPN security standard developed by IETF, working at the IP layer, providing the function of encrypting and authenticating IP packets.
- Used to protect data flows between a pair of hosts (host-to-host), a pair of security gateways (gateway-to-gateway), or between a host and a gateway (host-to-gateway).
- IPSec provides confidentiality, integrity, access control, and data source authentication security protection services for IP segments.
- IPSec is a protocol suite that includes mutual authentication protocols and key agreement protocols during session initialization, as well as protection (authentication and/or encryption) protocols for each IP packet during communication sessions.
SSL VPN (Secure Sockets Layer VPN)
- A mechanism for implementing VPN using the Secure Sockets Layer SSL protocol
- SSL protocol is typically built into browsers like IE. SSL VPN using SSL protocol for authentication and data encryption can be used without installing a client.
- SSL VPN is simple to deploy, but its performance is far lower than VPN implemented using IPSec.
Transport Layer Security Protocol TLS
How to implement authentication and confidential data transmission between two communicating applications on the Internet?
TLS Overview
TLS (Transport Layer Security) origin:
- TLS protocol is a security protocol for implementing confidential communication on the Internet
- TLS protocol was developed by IETF based on improvements to Netscape's SSL (Secure Socket Layer) protocol
- Netscape developed the SSL protocol for protecting Web communications in 1994 and renamed it TLS 1.0 when releasing SSL 3.1
- IETF published a Draft in 1997, and released TLSv1.0 (RFC 2246) in 1999
- IETF released TLS v1.1 (RFC 4363) in 2006
TLS Design Goals
TLS design goals are as follows:
- Cryptographic security: TLS is used to establish secure connections between communicating entities
- Interoperability: Independent developers can use TLS to develop applications without exchanging program code
- Extensibility: Provides a framework for conveniently adding new public key and symmetric cipher algorithms
- Relative efficiency: Cryptographic operations are highly CPU-intensive, especially public key operations. TLS provides a session caching mechanism to reduce the number of connections established, and minimizes network activity.
TLS Architecture
TLS architecture:
- TLS sits between the TCP layer and the application layer, transparent to the application layer. It establishes a reliable end-to-end secure service on top of the reliable transport protocol TCP, providing confidentiality and integrity protection for two communicating entities.
- TLS protocol is divided into two layers:
- Lower layer: Record protocol layer
- Upper layer: Handshake protocol layer
- TLS Record Protocol layer:
- The TLS record protocol is built on reliable TCP, providing data encapsulation for higher-layer protocols, implementing compression/decompression, encryption/decryption, and MAC computation/verification operations.
- The TLS record protocol uses cipher algorithms and keys negotiated by the TLS handshake protocol to encrypt upper-layer data for confidentiality. It also uses
HMACto achieve integrity of transmitted messages.
- TLS Handshake Protocol layer:
- Contains 3 sub-protocols: TLS handshake protocol, TLS cipher spec change protocol, TLS alert protocol
- The TLS handshake protocol layer is responsible for authentication between client and server, negotiating encryption algorithms and keys
- TLS protocol uses symmetric ciphers to encrypt transmitted data, and public key ciphers for identity authentication and exchanging encryption keys.
TLS Sessions and Connections
Two important concepts in TLS:
- TLS connection
- A connection is a transport that provides an appropriate type of service
- A TLS connection is an end-to-end relationship
- Connections are temporary; each connection is associated with one session
- TLS session
- A TLS session is an association between a client and a server
- Sessions are created by the handshake protocol, defining a set of cryptographic security parameters that can be shared by multiple connections
- Sessions are used to avoid the negotiation cost of providing new security parameters for each connection
Session States:
- Multiple states are associated with a session
- Once a session is established, there exists a current read or write state
- During the handshake protocol, pending read and write states are created
- When the handshake protocol succeeds, the pending state is converted to the current state
- Each session state is actually a set of parameters

喜欢的话,留下你的评论吧~